AES-NI
| What is AES-NI |
|---|

Intel‘s AES New Instructions AES-NI is a encryption instruction set that improves on the Advanced Encryption Standard (AES) algorithm and accelerates the encryption of data in many processor familys.
Comprised of seven new instructions, AES-NI gives your environment faster, more affordable data protection and greater security.
| Chapter |
|---|
Architecture:
R80.x Security Gateway Architecture (Logical Packet Flow)
R80.x Security Gateway Architecture (Content Inspection)
R80.x Security Gateway Architecture (Acceleration Card Offloading)
R80.x Ports Used for Communication by Various Check Point Modules
Performance Tuning:
R80.x Performance Tuning Tip – AES-NI
R80.x Performance Tuning Tip – SMT (Hyper Threading)
R80.x Performance Tuning Tip – Multi Queue
R80.x Performance Tuning Tip – Connection Table
R80.x Performance Tuning Tip – fw monitor
R80.x Performance Tuning Tip – TCPDUMP vs. CPPCAP
R80.x Performance Tuning Tip – DDoS „fw sam“ vs. „fwaccel dos“
Cheat Sheet:
R80.x cheat sheet – fw monitor
R80.x cheat sheet – ClusterXL
More interesting articles:
Article list (Heiko Ankenbrand)
| Appliances and Open Servers with AES-NI |
|---|
Better throughput can be achieved by selecting a faster encryption algorithm. For a comparison of encryption algorithm speeds, refer to sk73980 – Relative speeds of algorithms for IPsec and SSL.
AES-NI is Intel’s dedicated instruction set, which significantly improves the speed of Encrypt-Decrypt actions and allows one to increase AES throughput for:
- Site-to-Site VPN
- Remote Access VPN
- Mobile Access
- HTTPS Interception
The general speed of the system depends on additional parameters.
Check Point supports AES-NI on many appliances, only when running Gaia OS with 64-bit kernel. On these appliances AES-NI is enabled by default. AES-NI is also supported on Open Servers.
Affected encryption algorithms include:
- AES-CBC (128-bit and 256-bit)
- AES-GCM (128-bit and 256-bit), which shows the most significant improvement – with AES-NI, it is faster than AES-CBC, when both sides support AES-NI. Without AES-NI support, it is slightly slower than AES-CBC + HMAC-SHA1.
| Check if AES-NI is activated |
|---|
# dmesg | grep “AES-NI”
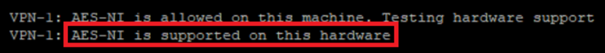
If it is not available, the following message is displayed:
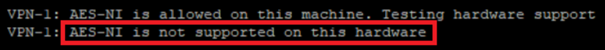
If AES-NI is not enabled, it must be turned on in the BIOS (if available). Typical way for Open Servers.
It can also be checked if the CPU provides AES-NI. For this the following command should be executed. Here “aes” should now be displayed.
# grep -m1 -o aes /proc/cpuinfo
![]()
| AES-NI performance measurement |
|---|
A little bit of reverse engineering.
Check Point uses OpenSSL as library. Therefore the command “openssl” is provided as “cpopenssl”. This gives us the possibility to execute all openssl commands. With this I tested a little bit and came to the conclusion that performance measurements are possible with the following command. So you can test the performance differences with enabled and disabled AES-NI.
Warning notice: If you execute this command you have 100% CPU usage on the firewall for 20 sec.
# cpopenssl speed aes-256-cbc
Enabled AES-NI:
![]()
Disabled AES-NI:
![]()
After these results I would always recommend to activate AES-NI and AES is preferred to 3DES because it offers many performance advantages through the hardware acceleration.
With the following command you can test and compare all encryption methods. After these results I would always recommend to activate AES-NI and AES is preferred to 3DES because it offers many performance advantages through the hardware acceleration.
Warning notice: If you execute this command you have 100% CPU usage for a long time!
# cpopenssl speed
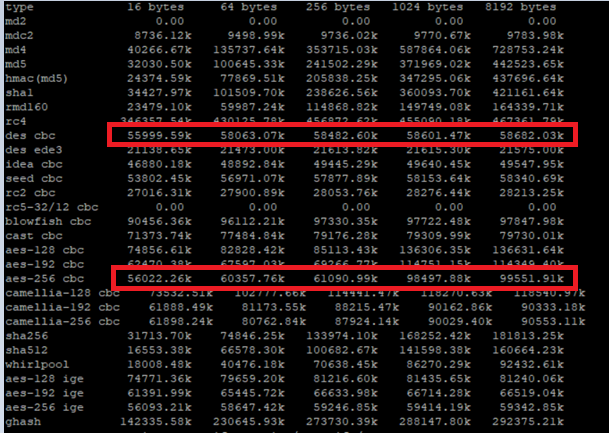
This makes it possible to compare encryption algorithms. It shows that e.g. AES 256 is more performant than DES. Therefore AES 256 should rather be used for VPN connections than DES or 3DES. This is also well described in the following SK Relative speeds of algorithms for IPsec and SSL.
| References |
|---|
Relative speeds of algorithms for IPsec and SSL
Best Practices – VPN Performance
vSEC Virtual Edition (VE) Gateway support for AES-NI on VMware ESX
Best Practices – VPN Performance
MultiCore Support for IPsec VPN in R80.10 and above
Copyright by Heiko Ankenbrand1994-2019
